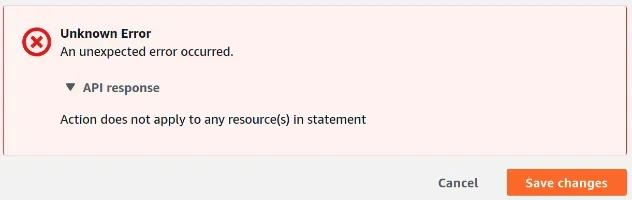
S3 Action does not Apply to any Resources Error [Solved]
Last updated: Feb 26, 2024
Reading time·3 min

# S3 Action does not Apply to any Resources Error
The "Action Does Not Apply to any Resources" S3 error occurs because we're
trying to attach a bucket policy with statements, where the specified Action
is not applicable to the specified Resource.
Actions, whose name includes the word Bucket (ListBucket, GetBucketPolicy,
GetBucketAcl) should be applied to a Resource of the bucket's ARN
(arn:aws:s3:::my-bucket).
Whereas actions, whose names include the word Object (GetObject,
PutObject, DeleteObject) should be applied to resources inside the bucket
(arn:aws:s3:::my-bucket/*).
To solve the error, set the Resource field of Bucket-specific actions to
the bucket's ARN (arn:aws:s3:::my-bucket) and the Resource field of
Object-specific actions to an ARN inside the bucket
(arn:aws:s3:::my-bucket/*).
The following bucket policy grants the
ListBucket and GetObject actions in two separate policy statements because
the Actions are applied to different Resources.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": "*", "Action": [ "s3:GetObject" ], "Resource": "arn:aws:s3:::YOUR_BUCKET_NAME/*" }, { "Effect": "Allow", "Action": [ "s3:ListBucket" ], "Principal": { "AWS": "arn:aws:iam::YOUR_ACCOUNT_NUMBER:user/YOUR_USERNAME" }, "Resource": "arn:aws:s3:::YOUR_BUCKET_NAME" } ] }
YOUR_BUCKET_NAME placeholder with the name of your bucket.We have 2 policy statements in the bucket example:
Allows the
GetObjectaction to all users (makes the bucket publicly readable). Notice that theGetObjectaction is applied on all resources inside of the bucket -arn:aws:s3:::YOUR_BUCKET_NAME/*.Allows the
ListBucketaction to a specific IAM user. Notice that theListBucketaction is applied to the bucket itselfarn:aws:s3:::YOUR_BUCKET_NAME.
If you were to add more actions that include Bucket, e.g.
ListBucketMultipartUploads or ListBucketVersions, they would have to have
the plain bucket ARN as a Resource.
Whereas, if you were to add more actions that include Object, e.g. PutObject
or DeleteObject, the Resource would have to be a path inside the bucket.
Actions do not apply to the specified Resources in the IAM policy. To solve the error, we have to correct the policy's Resource field.The easiest way to determine what the Resource field should look like is to
look at the
AWS S3 Actions table.
You can use ctrl + f to search for a specific action name and look at the
resource type for it.
For example, the ListBucket action has a Resource type of bucket:
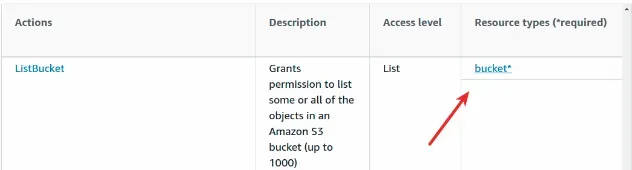
Notice that the resource type is a hyperlink. If you click on the link, you will
see the ARN that you have to specify as a Resource in the policy statement.
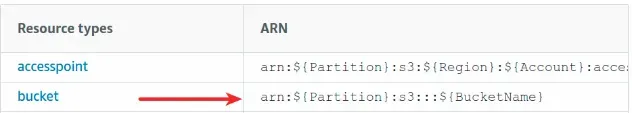
The ARN in the screenshot shows the complete Resource field template for the
ListBucket action. All we have to do is replace the ${Partition} placeholder
with aws and the ${BucketName} with the name of the bucket.
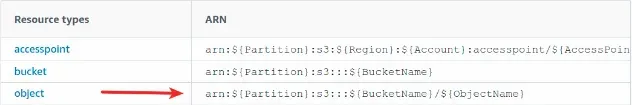
Similarly, if we look at the GetObject action, we will see that its
Resource type is object.
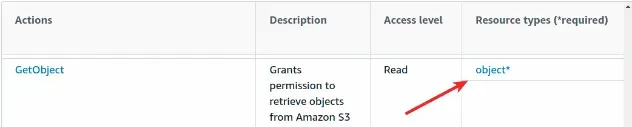
If we click on the hyperlink, the expected ARN template for the Resource field
is shown:
You can find a complete list of the Actions, Resources and condition keys for all services by clicking on this docs link.
# Additional Resources
You can learn more about the related topics by checking out the following tutorials:
- Get the Size of a Folder in AWS S3 Bucket
- How to Get the Size of an AWS S3 Bucket
- List all Files in an S3 Bucket with AWS CLI
- Configure CORS for an AWS S3 Bucket
- Allow Public Read access to an AWS S3 Bucket
- Copy a Local Folder to an S3 Bucket
- Download a Folder from AWS S3
- How to Rename a Folder in AWS S3
- How to Delete a Folder from an S3 Bucket
- Count Number of Objects in S3 Bucket
- AWS CDK Tutorial for Beginners - Step-by-Step Guide
- How to use Parameters in AWS CDK
- How to List all Resources in an AWS Account
- S3 Access Denied when calling ListObjectsV2 error [Solved]
- S3 Access Denied when calling PutObject

