S3 Access Denied when calling ListObjectsV2 error [Solved]
Last updated: Feb 26, 2024
Reading time·3 min
# S3 Access Denied when calling ListObjectsV2
The S3 error "(AccessDenied) when calling the ListObjectsV2 operation" occurs when we try to list the objects in an S3 bucket without having the necessary permissions.
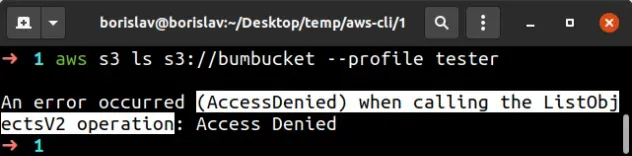
To solve the error attach a policy that allows the ListBucket action on the
bucket itself and the GetObject action on all of the bucket's objects to the
IAM entity (user or role) that is trying to access the S3 bucket.
Edit the IAM entity (user or role) that grants permissions to the bucket and add the following policy.
Make sure to replace the YOUR_BUCKET placeholder with the name of your
S3 bucket.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "s3:GetObject" ], "Resource": [ "arn:aws:s3:::YOUR_BUCKET/*" ] }, { "Effect": "Allow", "Action": [ "s3:ListBucket" ], "Resource": [ "arn:aws:s3:::YOUR_BUCKET" ] } ] }
The first statement in the JSON policy allows the GetObject action on
individual objects in sub-directories of the bucket.
The second statement in the policy allows the ListBucket action. It allows the
IAM entity to list all of the bucket's objects.
After attaching the IAM policy to the IAM user or role that tries to list the bucket's objects, the error should be resolved.
# Verify the bucket doesn't deny access to the ListBucket action
If the error is not resolved, you have to verify that the
bucket policy does not deny access to the
ListBucket or GetObject actions and that it does not have a condition that
only allows a specific IP range to access the bucket's objects:
Open your AWS S3 console and click on your bucket's name.
Click on the
Permissionstab and scroll down to theBucket Policysection.Verify that your bucket policy does not deny the
ListBucketorGetObjectactions. An explicitDenystatement always overridesAllowstatements.
If the bucket policy does not Deny the ListBucket or GetObject actions,
but you still are unable to list your bucket's objects, add the following Bucket
policy in the editor.
YOUR_BUCKET, YOUR_ACCOUNT_NUMBER, YOUR_USERNAME placeholders with real values.{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::YOUR_ACCOUNT_NUMBER:user/YOUR_USERNAME" }, "Action": "s3:GetObject", "Resource": "arn:aws:s3:::YOUR_BUCKET/*" }, { "Effect": "Allow", "Principal": { "AWS": "arn:aws:iam::YOUR_ACCOUNT_NUMBER:user/YOUR_USERNAME" }, "Action": "s3:ListBucket", "Resource": "arn:aws:s3:::YOUR_BUCKET" } ] }
We allowed the GetObject and ListObject actions to a specific user in the
account (the Principal field).
This policy allows an IAM user to invoke the
GetObject and ListObject actions on the bucket, even if they don't have a
policy that permits them to do that.
# Additional Resources
You can learn more about the related topics by checking out the following tutorials:
- Get the Size of a Folder in AWS S3 Bucket
- How to Get the Size of an AWS S3 Bucket
- Configure CORS for an AWS S3 Bucket
- Allow Public Read access to an AWS S3 Bucket
- Copy a Local Folder to an S3 Bucket
- Download a Folder from AWS S3
- How to Rename a Folder in AWS S3
- How to Delete a Folder from an S3 Bucket
- Count Number of Objects in S3 Bucket
- AWS CDK Tutorial for Beginners - Step-by-Step Guide
- How to use Parameters in AWS CDK
- Query Contains Examples with AWS CLI
- S3 Access Denied when calling PutObject
- S3 Action does not Apply to any Resources Error
- The Bucket you are attempting to Access AWS S3 Error [Fixed]

