How to add permissions to Lambda Functions in AWS CDK
Last updated: Jan 27, 2024
Reading time·4 min

# Table of Contents
- Adding Permissions to a Lambda Function in AWS CDK
- Deploying Additional Permissions for Lambdas in CDK
- Lambda Permissions in AWS CDK - Discussion
- The provided execution Role does not have Permissions
# Adding Permissions to a Lambda Function in AWS CDK
To add permissions to a Lambda Function, we have to attach a policy to the function's role.
Let's take a look at a complete example where we:
- Create a Lambda function.
- Create an IAM Policy statement.
- Attach an inline policy to the function's role, passing it the policy statement we created.
import * as iam from 'aws-cdk-lib/aws-iam'; import * as lambda from 'aws-cdk-lib/aws-lambda'; import {NodejsFunction} from 'aws-cdk-lib/aws-lambda-nodejs'; import * as cdk from 'aws-cdk-lib'; import * as path from 'path'; export class CdkStarterStack extends cdk.Stack { constructor(scope: cdk.App, id: string, props?: cdk.StackProps) { super(scope, id, props); // 👇 define the Lambda const myFunction = new NodejsFunction(this, 'my-function', { runtime: lambda.Runtime.NODEJS_18_X, handler: 'main', entry: path.join(__dirname, `/../src/my-lambda/index.ts`), }); // 👇 create a policy statement const s3ListBucketsPolicy = new iam.PolicyStatement({ actions: ['s3:ListAllMyBuckets'], resources: ['arn:aws:s3:::*'], }); // 👇 add the policy to the Function's role myFunction.role?.attachInlinePolicy( new iam.Policy(this, 'list-buckets-policy', { statements: [s3ListBucketsPolicy], }), ); } }
cdk-v1 branch in the GitHub repository.Let's go over what we did in the code sample:
- We defined a Lambda function via the NodejsFunction construct.
- We created an IAM Policy Statement with the PolicyStatement class. The policy grants the Lambda function access to list the S3 buckets in the account.
- We attached an inline IAM Policy to the function's role and we passed it the statement we created earlier.
# Table of Contents
- Deploying Additional Permissions for Lambdas in CDK
- Lambda Permissions in AWS CDK - Discussion
- The provided execution Role does not have Permissions
# Deploying Additional Permissions for Lambdas in CDK
I'll issue the deploy command.
npx aws-cdk deploy
The CloudFormation console shows that our list-buckets-policy has been
provisioned.
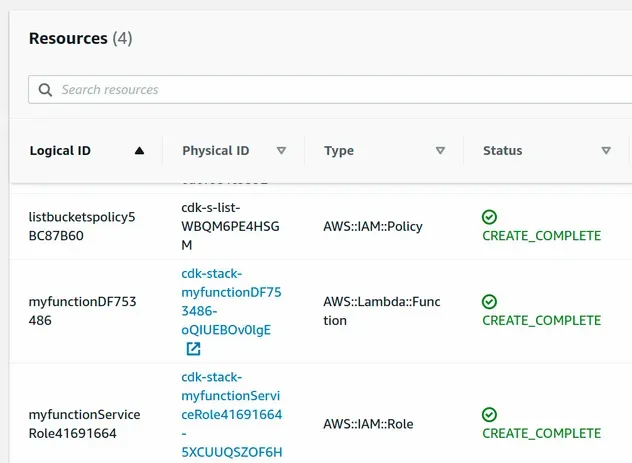
The IAM role of the lambda function now has 2 policies:
- The default
AWSLambdaBasicExecutionRolepolicy that is managed by AWS. - The
list-buckets-policyinline policy that is managed by us.
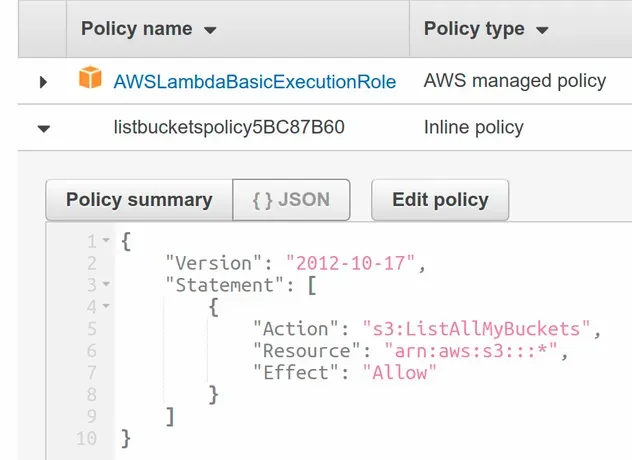
At this point, we've successfully added permissions to a Lambda function's role.
# Table of Contents
# Lambda Permissions in AWS CDK - Discussion
When we define a Lambda function, it comes with an automatically generated Role (unless we explicitly provide one). This role will then be assumed by the Lambda function during execution.
The automatically generated policy included in the role is called
AWSLambdaBasicExecutionRole. It grants permissions related to logging:
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "logs:CreateLogGroup", "logs:CreateLogStream", "logs:PutLogEvents" ], "Resource": "*" } ] }
In most of our lambda functions, we want to be able to log information to Cloud Watch, so extending the default Lambda role is a good option.
lambda.amazonaws.com to assume the role and add the logging permissions ourselves.The default trust relationship looks as follows.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Principal": { "Service": "lambda.amazonaws.com" }, "Action": "sts:AssumeRole" } ] }
By attaching an inline policy to the function's role, we were able to keep the default Lambda execution role and attach policies to extend it.
If we were to pass in our own role, we could add the
AWSLambdaBasicExecutionRole policy to it in the following way.
const myFunction = new NodejsFunction(this, 'my-function', { // ... rest role: someRole, }); myFunction.role?.addManagedPolicy( iam.ManagedPolicy.fromAwsManagedPolicyName( 'service-role/AWSLambdaBasicExecutionRole', ), ); // only required if your function is in a VPC myFunction.role?.addManagedPolicy( iam.ManagedPolicy.fromAwsManagedPolicyName( 'service-role/AWSLambdaVPCAccessExecutionRole', ), );
I've also written a guide on how to provision and configure lambda functions in AWS CDK.
# The provided execution Role does not have Permissions
Attach the AWSLambdaVPCAccessExecutionRole managed policy to the function's
execution role to solve the lambda error "The provided execution role does not
have permissions to call DescribeNetworkInterfaces".
The error occurs because lambda functions in a VPC need to have permission to create and manage elastic network interfaces.
To attach the AWSLambdaVPCAccessExecutionRole policy to the function, you have
to:
- Open the AWS Lambda console and click on the function's name
- Click on the
ConfigurationTab and then clickPermissions
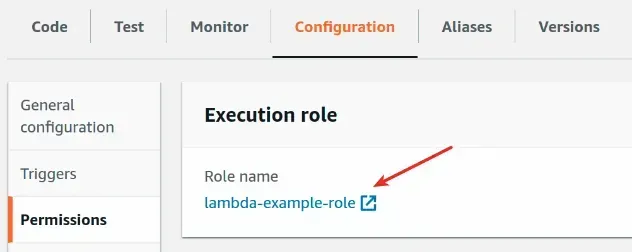
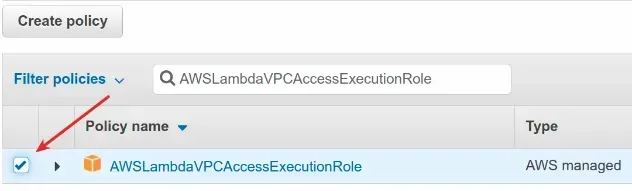
- Click on the function's role and then click
Add permissionsandAttach policies - Filter for the
AWSLambdaVPCAccessExecutionRolemanaged policy, click the checkbox next to its name and clickAttach Policy
The AWSLambdaVPCAccessExecutionRole grants the lambda function permissions to
create and manage elastic network interfaces and log to CloudWatch.
{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "logs:CreateLogGroup", "logs:CreateLogStream", "logs:PutLogEvents", "ec2:CreateNetworkInterface", "ec2:DescribeNetworkInterfaces", "ec2:DeleteNetworkInterface", "ec2:AssignPrivateIpAddresses", "ec2:UnassignPrivateIpAddresses" ], "Resource": "*" } ] }
After the function has permission to create and manage Elastic network interfaces, the error will be resolved.
print statement in the function's code and click on the Deploy button.# Additional Resources
You can learn more about the related topics by checking out the following tutorials:
- Write TypeScript Lambda functions in AWS CDK - Complete Guide
- Configure Lambda Log Retention in AWS CDK
- Create Lambda Functions in a VPC in AWS CDK
- How to use Lambda Layers in AWS CDK - Complete Guide
- AWS CDK Tutorial for Beginners - Step-by-Step Guide
- How to use Context in AWS CDK
- How to use Parameters in AWS CDK
- Cannot find module (AWS Lambda Error) [Solved]
- AWS Lambda Task timed out error [Solved]

