The Security Token included in the Request is Invalid
Last updated: Feb 26, 2024
Reading time·3 min

# The Security Token included in the Request is Invalid
The error "the Security Token included in the Request is Invalid" can occur for multiple reasons:
- The user's credentials are inactive. Open the IAM console, click on the
user, and in the
Security Credentialstab, make sure the security credentials of the user are active.
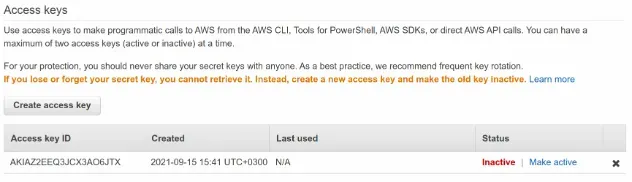
The user's access key ID and/or secret access key are incorrect. Verify that the values of your Access key and Secret access key are correct. In case you don't have them, generate new ones and make sure to delete the old keys.
The AWS CLI resolves the credentials in the following order:
- It looks for the environment variables
AWS_ACCESS_KEY_IDandAWS_SECRET_ACCESS_KEY. - In case the environment variables are not set, it looks in:
~/.aws/credentialson Linux and MacOS and inC:\Users\USERNAME\.aws\credentialson Windows.
- It looks for the environment variables
The user has forgotten to specify the correct
--profileparameter in the call to the AWS CLI (in cases where the default profile is not the desired caller).
The user has switched from temporary MFA (multi-factor authentication) Credentials to User credentials, but has forgotten to unset the
AWS_SESSION_TOKENenvironment variable or theaws_session_tokensetting in thecredentialsfile.The user has Multi-Factor Authentication enabled, but has not set a valid session token in the
AWS_SESSION_TOKENenvironment variable oraws_session_tokensetting in thecredentialsfile.
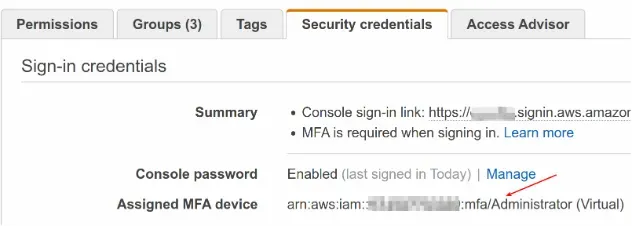
- To generate temporary MFA credentials, open the IAM console and click on the
user. Then copy the MFA device ARN because it's required in the call to the
get-session-tokenAPI:
Other than the MFA device ARN, you will need an MFA Token from your authenticator app, f.e. Google Authenticator (Most likely a 6-digit code, e.g. 001219).
Once you have the MFA device ARN and the MFA Token, call the
get-session-tokenAPI as follows.
aws sts get-session-token --serial-number MFA_DEVICE_ARN --token-code MFA_TOKEN_CODE
- The output from the call to the
get-session-tokenwill look similar to this.
{ "Credentials": { "SecretAccessKey": "secret-access-key", "SessionToken": "temporary-session-token", "Expiration": "expiration-date-time", "AccessKeyId": "access-key-id" } }
- To update the credentials in your
credentialsfile, run theaws configurecommand. The command allows you to set the Access key and Secret access key values, and then you have to also set the session token:
# for default profile aws configure # for profile named admin aws configure --profile admin # set the session token for default profile aws configure set aws_session_token YOUR_SESSION_TOKEN # set the session token for a profile named admin aws configure set aws_session_token YOUR_SESSION_TOKEN --profile admin
By default, the session token is temporary and valid for 12 hours.
If you prefer the Environment variable approach, set the following environment variables:
# on Linux and macOS export AWS_ACCESS_KEY_ID=YOUR_ACCESS_KEY_ID export AWS_SECRET_ACCESS_KEY=YOUR_SECRET_ACCESS_KEY export AWS_SESSION_TOKEN=YOUR_SESSION_TOKEN # or on Windows setx AWS_ACCESS_KEY_ID=YOUR_ACCESS_KEY_ID setx AWS_SECRET_ACCESS_KEY=YOUR_SECRET_ACCESS_KEY setx AWS_SESSION_TOKEN=YOUR_SESSION_TOKEN
You can issue these commands in bash or zsh on macOS and Linux or in CMD
(Command Prompt) on Windows.
Alternatively, you can add the lines to your profile file to set the environment variables every time your PC is booted.
On MacOS and Linux, you can find your profile file at ~/.bashrc,
~/.bash_profile or ~/.zshrc.
# Additional Resources
You can learn more about managing your AWS credentials and using the AWS CLI by checking out the following tutorials:
- Manage Multiple Accounts with the AWS CLI
- Set your Default Profile's Name in AWS CLI
- How to Clear your AWS CLI Credentials
- How to Get your Account Id with AWS CLI
- View your AWS CLI logs in Real Time (tail)
- How to turn off the Pager in AWS CLI
- Create a Role with AWS CLI - Complete Guide
- Create a Lambda Function with AWS CLI - Complete Guide
- Invoke Lambda Functions with AWS CLI - Complete Guide
- Tag an S3 Bucket with AWS CLI
- AWS CDK Tutorial for Beginners - Step-by-Step Guide
- How to use Parameters in AWS CDK
- SignatureDoesNotMatch Error in AWS CLI [Solved]

