Grant AWS Lambda Access to an SQS Queue or SNS Topic
Last updated: Feb 26, 2024
Reading time·6 min

# Table of Contents
Note: if you need to grant AWS Lambda access to an SNS topic, click on the second subheading.
# Grant AWS Lambda Access to an SQS Queue
To grant a Lambda function access to an SQS queue, we have to attach an IAM policy to the function's execution role.
The policy should grant permissions for all the Actions the function needs
to perform on the queue.
For example, the following policy grants permissions for the most commonly used SQS actions on a specific SQS queue.
YOUR_* placeholders in the Resource element with the real values.{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "sqs:SendMessage", "sqs:DeleteMessage", "sqs:ChangeMessageVisibility", "sqs:ReceiveMessage", "sqs:TagQueue", "sqs:UntagQueue", "sqs:PurgeQueue" ], "Resource": "arn:aws:sqs:YOUR_REGION:YOUR_ACCOUNT_NUMBER:YOUR_QUEUE_NAME" } ] }
The Resource element is simply the SQS queue's ARN. It should look like
arn:aws:sqs:us-east-1:123456789:my-queue once the real values are in place.
The actions your Lambda function needs to perform on the queue are use-case dependent.
"sqs:*" for the Action element in the policy to grant full SQS access to the Lambda function. However, it's best practice to grant an entity the least permissions that get the job done.You can view a full list of the SQS Actions in the
SQS actions table.
There is a Description column that explains what each action does.
To attach a policy to the Lambda function's execution role, you have to:
- Open the AWS Lambda console and click on your function's name.
- Click on the
Configurationtab and then clickPermissions.
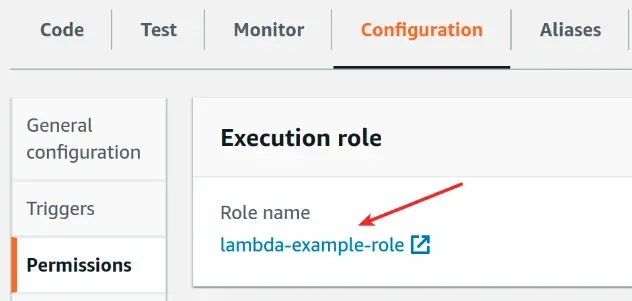
- Click on the function's role.
- Click on
Add permissionsand then clickCreate inline policy.
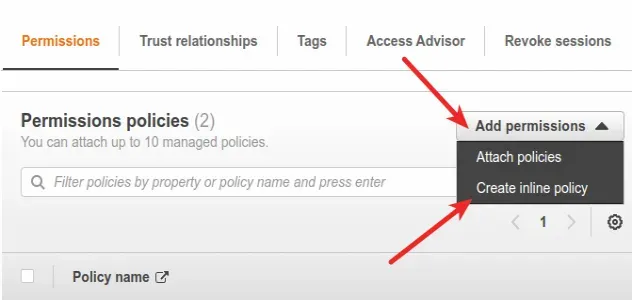
- In the
JSONeditor paste the following policy.
YOUR_* placeholders and adjust the Actions your Lambda function needs to execute.{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "sqs:SendMessage", "sqs:DeleteMessage", "sqs:ChangeMessageVisibility", "sqs:ReceiveMessage", "sqs:TagQueue", "sqs:UntagQueue", "sqs:PurgeQueue" ], "Resource": "arn:aws:sqs:YOUR_REGION:YOUR_ACCOUNT_NUMBER:YOUR_QUEUE_NAME" } ] }
- Click
Review Policyand give your policy a name, then clickCreate policy.
At this point, the Lambda function's role has been extended with a policy that grants access to some SQS actions on a specific queue.
Invoke your lambda function and verify whether it has access to the SQS queue.
If your function is still unable to access the SQS queue, try to increase the
function's timeout by a second in the AWS console, or simply add an extra
print statement in the code and click the Deploy button.
If your Lambda function still doesn't have access to the queue, expand the IAM policy you added to the function's role and edit it to look like the policy below.
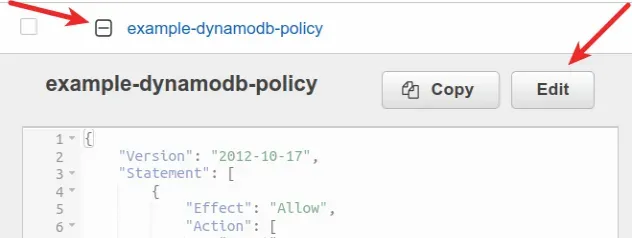
YOUR_* placeholders with the real values.{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "sqs:*" ], "Resource": "arn:aws:sqs:YOUR_REGION:YOUR_ACCOUNT_NUMBER:YOUR_QUEUE_NAME" } ] }
The IAM policy grants full access to an SQS queue.
Your Lambda function will be able to execute all SQS actions on the queue.
* symbol is useful when debugging.After you've updated the policy, try to invoke your Lambda function again. It should have permission to execute any action on the SQS queue.
After you verify which actions your lambda needs to run, you can make the IAM policy less permissive.
Deny effect will always override any Allow statements.# Grant AWS Lambda Access to an SNS Topic
To grant a Lambda function access to an SNS topic, we have to attach an IAM policy to the function's execution role.
The policy should grant permissions for all the Actions the function needs
to perform on the topic.
For example, the following policy grants permissions for the most commonly used SNS actions on a specific SNS topic.
YOUR_* placeholders in the Resource element with the real values.{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "sns:Publish", "sns:Subscribe", "sns:CreateTopic", "sns:GetTopicAttributes", "sns:SetTopicAttributes", "sns:TagResource", "sns:UntagResource", "sns:ListTagsForResource", "sns:ListSubscriptionsByTopic" ], "Resource": [ "arn:aws:sns:YOUR_REGION:YOUR_ACCOUNT_NUMBER:YOUR_TOPIC_NAME" ] } ] }
sns:Publish action in the Action list of the policy.The Resource element is simply the SNS topic's ARN, which you can copy from
the AWS SNS console.
It should look something like arn:aws:sns:us-east-1:123456789:my-topic once
the real values are in place.
The actions your lambda function needs to perform on the topic are use-case dependent.
"sns:*" for the Action element in the policy to grant full SNS access to the lambda function. However, it's a best practice to grant an entity the least permissions that get the job done.You can view a full list of the SNS Actions in the
SNS actions table.
There is a Description column that explains what each action does.
To attach a policy to the lambda function's execution role:
- Open the AWS Lambda console and click on your function's name.
- Click on the
Configurationtab and then clickPermissions.
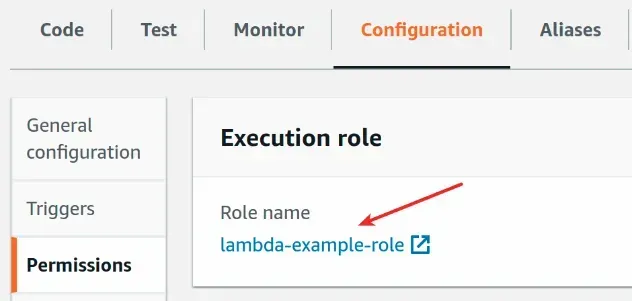
- Click on the function's role.
- Click on
Add permissionsand then clickCreate inline policy.
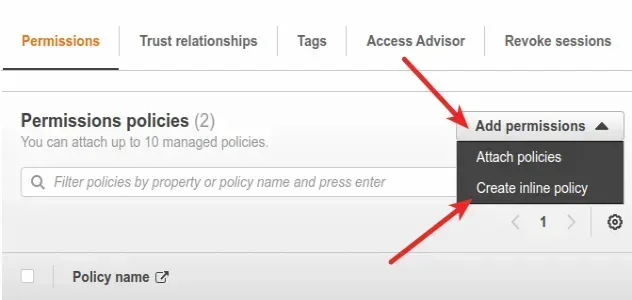
- In the
JSONeditor paste the following policy.
YOUR_* placeholders and adjust the Actions your lambda function needs to execute.The
Resource element is simply the topic's ARN, which you can copy from the AWS SNS console.{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "sns:Publish", "sns:Subscribe", "sns:CreateTopic", "sns:GetTopicAttributes", "sns:SetTopicAttributes", "sns:TagResource", "sns:UntagResource", "sns:ListTagsForResource", "sns:ListSubscriptionsByTopic" ], "Resource": [ "arn:aws:sns:YOUR_REGION:YOUR_ACCOUNT_NUMBER:YOUR_TOPIC_NAME" ] } ] }
- Click
Review Policyand give your policy a name, then clickCreate policy.
At this point, the Lambda function's role has been extended with a policy that grants access to some SNS actions on a specific topic.
Invoke your lambda function and verify whether it has access to the SNS topic.
If your function is still unable to access the SNS topic, try to increase the
function's timeout by a second in the AWS console or simply add an extra
print statement in the code and click the Deploy button.
If your Lambda function still doesn't have access to the topic, expand the IAM policy you added to the function's role and edit it to look like the policy below.
YOUR_* placeholders with real values.{ "Version": "2012-10-17", "Statement": [ { "Effect": "Allow", "Action": [ "sns:*" ], "Resource": [ "arn:aws:sns:YOUR_REGION:YOUR_ACCOUNT_NUMBER:YOUR_TOPIC_NAME" ] } ] }
The IAM policy above grants full access to an SNS topic. Your lambda function will be able to execute all SNS actions on the topic.
* symbol is useful when debugging.After you've updated the policy, try to invoke your Lambda function again. It should have the necessary permissions to execute any action on the SNS topic.
You can make the IAM policy less permissive after you verify which actions your lambda needs to run.
Deny effect will always override any Allow statements.I've also written a tutorial on how to add permissions to Lambda functions in AWS CDK.
# Additional Resources
You can learn more about the related topics by checking out the following tutorials:

