KMS Key Example in AWS CDK - Complete Guide
Last updated: Jan 26, 2024
Reading time·3 min

# Creating a KMS Key in AWS CDK
AWS KMS is a service that enables us to control access to our data by encrypting it with AWS-managed keys.
We are going to create and configure a KMS key in CDK and use it to encrypt an S3 bucket.
I'll post the complete code snippet and then we'll go over the code.
import * as kms from 'aws-cdk-lib/aws-kms'; import * as s3 from 'aws-cdk-lib/aws-s3'; import * as cdk from 'aws-cdk-lib'; export class CdkStarterStack extends cdk.Stack { constructor(scope: cdk.App, id: string, props?: cdk.StackProps) { super(scope, id, props); const key = new kms.Key(this, 'my-kms-key', { removalPolicy: cdk.RemovalPolicy.DESTROY, pendingWindow: cdk.Duration.days(7), alias: 'alias/mykey', description: 'KMS key for encrypting the objects in an S3 bucket', enableKeyRotation: false, }); const s3Bucket = new s3.Bucket(this, 'my-bucket', { removalPolicy: cdk.RemovalPolicy.DESTROY, encryption: s3.BucketEncryption.KMS, // 👇 encrypt with our KMS key encryptionKey: key, }); new cdk.CfnOutput(this, 'key-arn', { value: key.keyArn, }); new cdk.CfnOutput(this, 'bucket-name', { value: s3Bucket.bucketName, }); } }
Let's go over what we did in the code sample:
- We created a KMS key by instantiating the Key class. We passed the following props to the constructor:
| Name | Description |
|---|---|
removalPolicy | specify what should happen to the key when the stack is deleted. By default, the key is retained in an orphaned state |
pendingWindow | the number of days (7 - 30) before the KMS key gets deleted. By default the waiting period is 30 days |
alias | an alias to add to the KMS key. The alias can then be used for different operations, i.e. to import the KMS key in a different stack |
description | a short description of how the KMS key is intended to be used |
enableKeyRotation | whether AWS should rotate the KMS key for us |
We created an S3 bucket, for which we configured server-side encryption via the KMS key.
We created some
Outputsthat will help us identify the resources after we deploy the stack.
I'll deploy the resources from the stack and redirect the outputs to a file on the local file system.
npx aws-cdk deploy \ --output-file ./cdk-outputs.json
We've successfully created a symmetric KMS CMK (customer master key). A single symmetric KMS key is used to both encrypt and decrypt data.
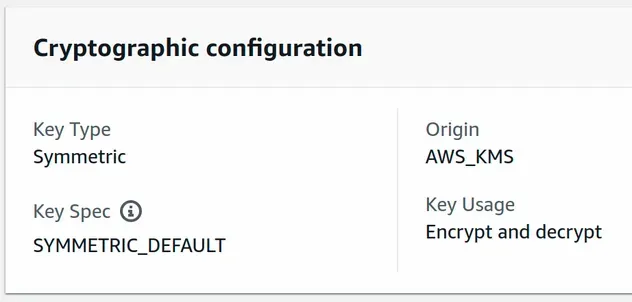
We can also see that CDK created a default key policy for us because we didn't specify one.
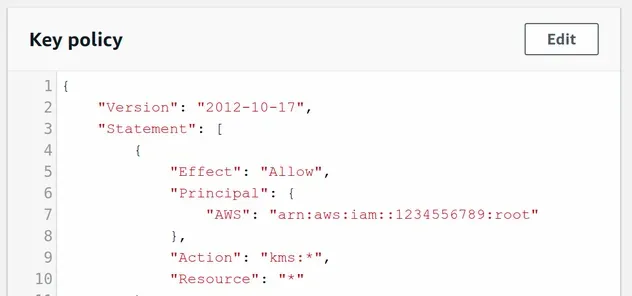
The default KMS Key Policy gives complete access to the root user to perform any KMS actions with the key.
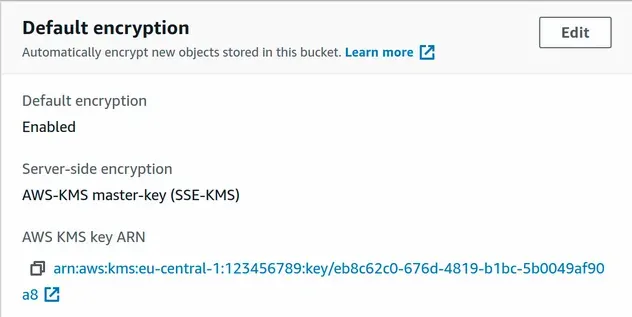
If we now take a look at the S3 bucket's encryption configuration, we can see that the objects in the bucket will get encrypted by the KMS key we created.
# Clean up
To delete the provisioned resources, execute the destroy command:
npx aws-cdk destroy

